Encryption and authentication platform for validated transactions.
A patent-pending solution for centralized authentication and secure encryption of personal identifiable information (PII), photos, latent biometric images, entire documents, tickets, payment cards and medical data.
Technology
Innovative technology for data storage. We have created a solution to the problems of digital data storage. You can protect your data with our innovative and best technology.
Technology
A rapid sequence of QR codes is recorded and displayed in video format, enabling the 1-second encryption and error-free transmission of large amounts of data in an animation burst.
As long as data is authenticated at the source (government, authorized issuer), we can guarantee the safe dissemination of the Motion QR cryptograms we generate. Authentication takes place on a physically guarded hardware security module (HSM) placed in customer’s infrastructure.

Authentication
Possible to authenticate whether any document has expired or been modified

Encryption
Cryptographic keys do not need to be re-encoded or updated, they don’t expire
How large amounts of data are transmitted?
Individual QR codes are overlaid, one on top of another and replayed in a sequential infinite loop as a video image, changing every tenth of a second.
While traditional QR codes have content limitations, 3D QR codes stacked and played as a 25 fps (frame per second) video can be processed by mobile phones in a matter of seconds or less.
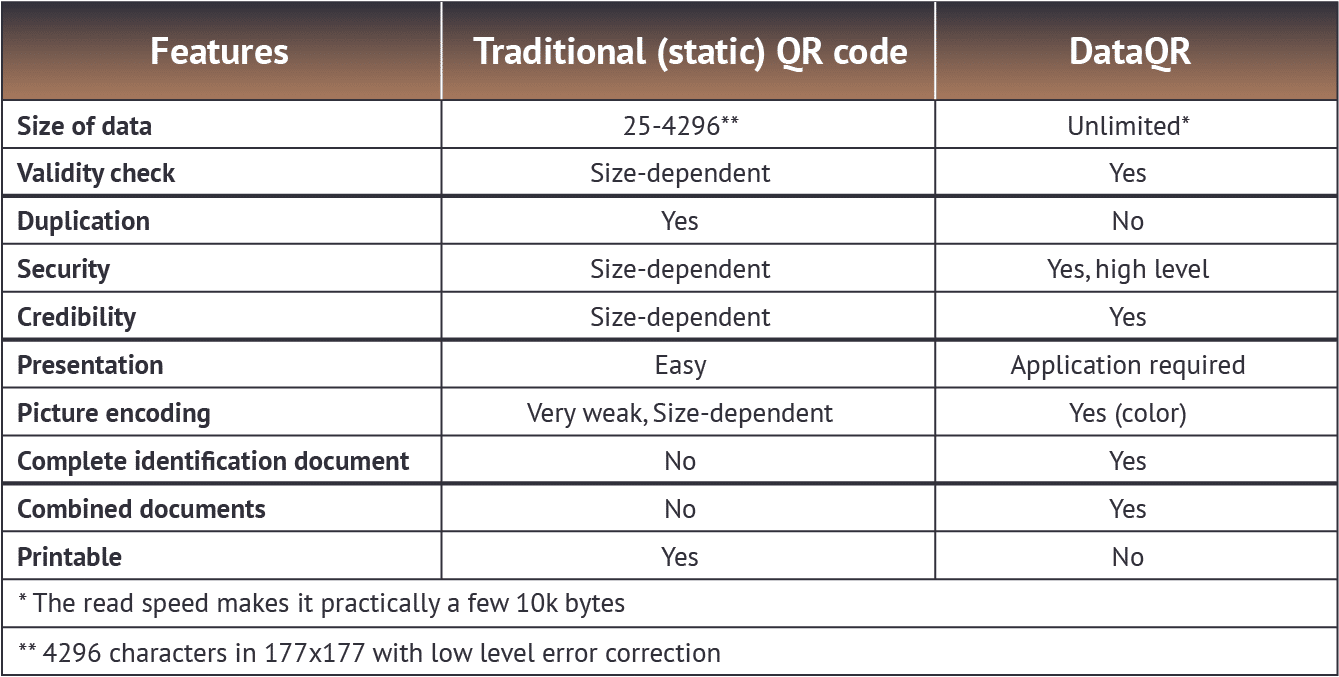
More About DataQR
Learn more about DataQR and our solutions and technology. We guarantee credibility.
The Technology
Security
Cybersecurity
Blockchain
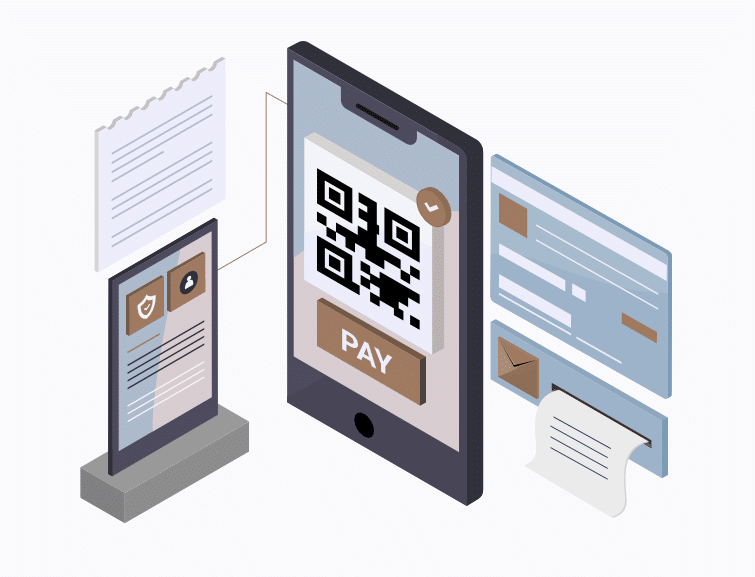
Applications
Digital documents that may be displayed in the DataQR system: personal identifiable information (PII), photos, biometric identifiers (latent biometric images), identity documents, driver’s license, medical documents, tickets, coupons, entire contracts or certificates as an image, payment cards, real estate title, stock certificates, medical data; essentially any document which reflects user’s financial, academic, medical, legal, or other status, as maintained by issuer.
Benefits
Flexible
Access levels can be set for modular disclosure of information on a need-to-know basis (Different access may be provided to immigration officers and restaurant owners, for example).
PRIVACY
Personal data remains with the user, is not stored in a central database, database not shared, no compliance risk as customer does not store data, users store their own data.
Versatile use
Several documents can be chained into one string (connect medical data to person, no need to validate and connect two separate documents).
Portability
Public keys are distributed widely on mobile devices, app securely updated with public keys released by document issuers on a regular basis.
Security
Combination of asymmetric encryption technologies, including 1024-4096-bit RSA and a transport encryption to carry the public key.
Easily updateable
Document expiry and modifications immediately reflected in system upon central authentication.
Offline use
Authentication can be performed using offline devices.
Authenticity
Guaranteed by the cryptographic structure.
BLOCKCHAIN & CYBERSECURITY
Blockchain
DataQR technology can be connected to blockchain projects very well because it makes sense to enter data into an immutable blockchain once the data has been verified. The verification process is what DataQR performs, essentially creating a zero trust environment. The blockchain keeps a verifiable lasting record and searchable history of any modification, authentication, or transaction of the data.
If parties wish to register the fact and nature of the transactions, but not the personal data itself in the public blockchain, it is enough to keep the DataQR codes in the blockchain, which provide a high enough level of encryption for only the stakeholders with the necessary keys to access the data.
A blockchain entry is made for each operation. This should be considered as part of the basic document. The blockchain ID can be viewed on the verification devices.
This process ensures the authenticity of the sequential order, traceability, and creation of the documents.
Cybersecurity
Upon User’s request a preventive threat intelligence layer is added to the real-time authentication of data as the personal identifiable information (PII) and digital footprint (email addresses and registered accounts) of the user is checked against dark web breached credential databases for exposure.
The nature of the data can be names, user names, email addresses, passwords, home addresses, telephone numbers, utility accounts, IP addresses, information about the software and hardware environment, bank account numbers, credit card details, social security numbers, mother’s maiden name, information about family members, hobbies, political or religious affiliation, job titles, places of employment, intellectual property, brands, trademarks, blueprints, strategic documents, contracts, confidential files, medical records, medical prescriptions, travel records, financial information, assets, investments, digital wallets, private keys, file hashes, legal documents, original copies, biometric images, academic records, real estate title deeds, stock certificates, paper assets, client data, and other sensitive databases.
If a match is found, indicating User’s data has been leaked, User is immediately alerted and the necessary steps can be taken to mitigate the risk of social engineering, identity theft or fraud.
Adequate warning can be given to organizations before a supply chain incident, ransomware attack, credential leak, insider threat, or a coordinated cyber attack using tools and malware specifically developed to breach their hardware and software environment unfolds.
ABOUT US
The team behind DataQR boasts many years of experience in the protection of critical infrastructure, access control, payment systems, and cybersecurity, including industrial honeypots, Advanced Persistent Threat (APT) groups, financial fraud detection, mapping of hacking behavior.
Contact Us to Get Started!
If you have any questions or concerns, please fill out the form and our team will contact you as soon as possible.