Our solution
The Solution for Data Storage
DataQR has introduced a more secure way of authentication using existing infrastructure and a paradigm shift in the way user data is communicated.
THE PROBLEM
When an identity document (or certificate, signed contract, or even legal tender) is presented to a controlling entity, how can they be sure it is authentic?
Digital documents are facing a similar challenge of trying to prevent copies, with elaborate encryption technology, third-party authentication and certification regimes, time-stamped digital signatures, blockchain, and using AI for data consistency checks.
Whether it is secure paper or immutable digital transactions, as long as the incentive of financial gain or power remains in place, there will always be a constant battle between developers and threat actors. New ways of forgery and hacking are being revealed every day, as the alarmingly growing number of attack tools, ransomware as well as leaked databases of credentials prove.
Centralized databases of customer data are sitting ducks for hackers.
Controlling entities must maintain an ever-increasing database of decryption methods as well as distinct feature sets updated from every issuer whose documents they handle. Banks, embassies and law firms often resort to apostilled documents to ensure the authenticity of locally issued documents using the services of a public notary.
Current systems of authentication are
Expensive
Resource - intensive
Prone to human error
Difficult to control
Time - consuming
THE SOLUTION
DataQR has introduced a more secure way of authentication using existing infrastructure and a paradigm shift in the way user data is communicated.
The proliferation of mobile devices equipped with cameras capable of recording vast amounts of encrypted data within seconds makes it possible to operate a three-party global system of digital document control.
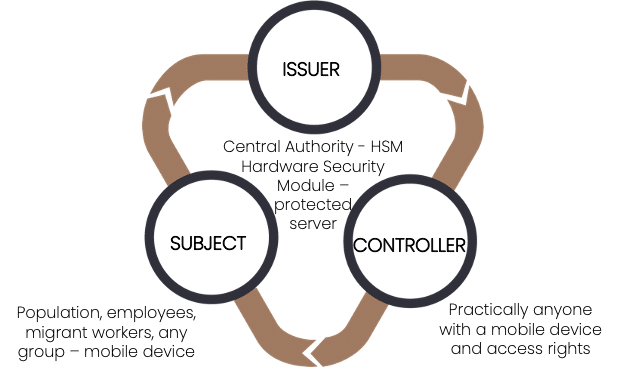
Data resides with the Users, who voluntarily select which item of information (document) they wish to share with Controlling entity. Just like showing your photo ID and debit card to the staff at a coffee shop, or showing your passport and boarding pass to personnel at the airport. Users tap images of the respective documents on their screen which are automatically turned into a moving QR image in the DataQR application for the Controlling entity to scan. The Controlling entity captures the QR image with the DataQR app on their mobile device. Note this can be performed remotely as well, during a video call.
Images of User’s documents will only appear on Controlling entity’s screen if all three of the following conditions have been fulfilled.
Condition 1
Condition 2
Condition 3

User presents the encrypted data, Issuer provides the public key, and Controlling entity is able to see the data and at the same time receive a real-time authentication of it from Issuer.
The very fact that the images of the documents appear on Controlling entity’s screen are proof of their authenticity, there is no other way the public key received from Issuer would have worked on Controlling entity’s device.
It is possible to control how much of each document appears on Controlling entity’s device, based on Controlling entity’s access level, so only data relevant to the transaction is displayed.
It is up to Controlling entity’s decision and binding legal requirements whether to proceed with the inspection of physical documents as well by comparing them to the digital images, or employ other methods of verification in addition to the DataQR verification.
