SECURITY
Secure – Cannot be Replicated, Forged, Modified
RSA, the algorithm by Rivest–Shamir–Adleman, is an asymmetric cryptographic algorithm. The Public Key can be known to everyone and is used to encrypt messages.
- RSA is an asymmetric encryption procedure. This means that the encryption key and the decryption key are not the same
- Modified RSA: RSA broken up and re-encrypted
- Data encrypted with the private key can only be successfully decrypted with the Public Key
- The Private Key is what is protected in the Hardware Security Module (HSM)
- The Public Key can be transferred. In possession of the Public Key, the holder is unable to generate a message (cryptogram) as if it had been created by the Private Key
- Therefore, if we successfully decrypt a message with a Public Key, we can know that the message was created with its private pair (In our case it was done by the HSM)
- This gives the system authenticity, as a successfully decoded message can only come from a strictly protected and controlled environment
- If someone successfully decrypts the message, they can be sure that it is from the original, protected environment
- Cryptographic keys do not need to be re-encoded or updated, they don’t expire
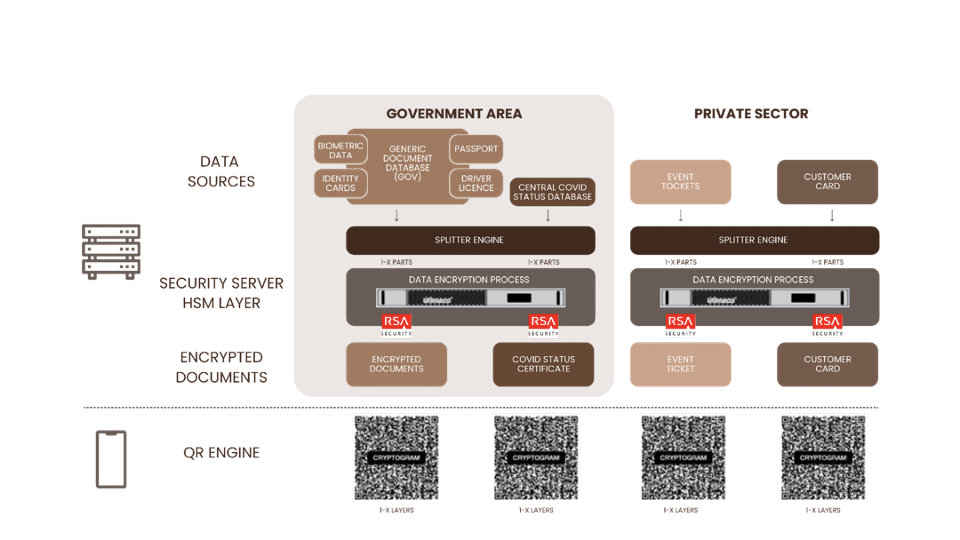
Document Encryption Process
1) The document is generated in the AC (Authority Center) marked Data Sources in the diagram.
2) The document is divided into packets of appropriate size for the cryptographic operation. Splitter Engine
3) We hand it over to the Hardware Security Module (HSM), indicating our requirements: RSA-4096
4) The HSM performs the transformation and returns the encrypted data packet.
The private key is never removed from the HSM. Nobody can know it!
5) This operation is performed until all data packets have been completed for the given document.
6) All encrypted data packets are sent to the mobile phone of the properly registered user.
7) The mobile phone generates QR codes from the data packets and presents them in a continuous loop according to a defined frame rate.
8) The verification device processes the video displayed on the screen of the presentation device.
9) It decrypts the data packets thus obtained if it has the public key (the private key pair of the encryptor) required for decryption. [The public key is issued by the HSM upon creating the key pair] They only have the required public key if they have permission to access that particular document.
10) The decoded data packets are arranged in order and collated.
11) Only then is the current document displayed.
Creating a key pair in the HSM is a discrete operation.
If a new document type is added to the system, the first step is to create a key pair with the HSM.
Decryption Process – Control & Validation
Offline verification of documents is possible anywhere and anytime
Result of document validation appears on control device
Each country or issuer could have their own private keys and publish their public keys in an updateable app.
Everyone with a mobile phone who downloads the app could verify authenticity of any user’s documents which are presented in the form of digital QR codes on user’s mobile device.
Contact Us to get started
If you have any questions or concerns, please fill out the form and our team will contact you as soon as possible.
